“PoW (Proof-of-Work) makes for a fairer coin distribution as everyone has to compete on equal terms. A constant reward, resulting in linear emission, extends this fair competition across all times.”
John Tromp
Key Takeaways
- Cuckoo Cycle is memory-bound Proof of Work mining algorithm that tries to find a cycle within a particular type of graph, a bipartite graph.
- There are a few projects that are implementing Tromp’s Cuckoo Cycle mining algorithm. MimbleWimble, the privacy preserving Blockchain protocol also makes use of Cuckoo Cycle. Aeternity, the unicorn Blockchain project based in Liechtenstein is using Cuckoo Cycle, and the hot privacy coins like Grin.
- MimbleWimble is a privacy preserving blockchain protocol implementation and gets its name from the Harry Potter fictional book series.
John Tromp from Cuckoo Cycle
John Tromp (1) is the inventor of the Cuckoo Cycle (2) mining algorithm, and its variants (Cuckatoo Cycle and Cuckaroo Cycle). He is also a core developer of the privacy focused blockchain Grin (3), which makes use of the MimbleWimble (4) protocol, a privacy preserving blockchain protocol. MimbleWimble implements his Cuckoo Cycle (5) mining algorithm. In addition, Tromp is known for having created a mining software implementation, or solver, of the Equihash (6) mining algorithm for Zcash (7). Tromp is one of the most intelligent computer scientists in the crypto space. Tromp has a PhD from the University of Amsterdam in Theoretical Computer Science and has an exceptional knack for bringing that theory into reality with practical algorithm implementations and computer code. Not only is he one of the brightest minds, he is also one of the humblest.
What is Cuckoo Cycle?
According to Tromp, Cuckoo Cycle is memory-bound Proof of Work mining algorithm that tries to find a cycle within a particular type of graph, a bipartite graph. In the case of Cuckoo Cycle, memory-bound means that the rate of solutions a miner can achieve depends on the memory bandwidth of the miner, as opposed to the amount of memory, or the amount of processing power of a miner. A graph, in simple terms, is a set of points connected with lines. A bipartite graph is two sets of points, where there are no lines between points within that particular set, only lines connecting points across the two different sets. When the lines across sets form a cycle, or in other words a loop, that cycle is known as a bipartite graph.
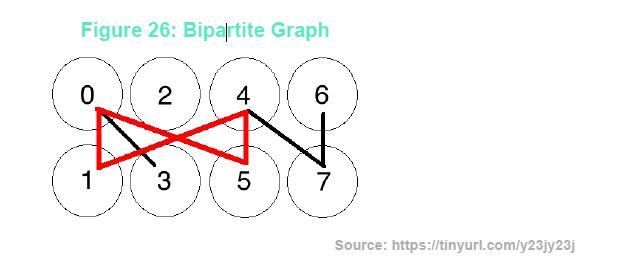
Tromp compared Cuckoo Cycle to Bitcoin’s Hashcash (8) mining algorithm and described Cuckoo Cycle as more of a stronger “Proof of Work” than Bitcoin’s Hashcash, which claims to be “Proof of Work” because of the tremendous amount of work that must be computed in order to find a solution. Instead Tromp described Hashcash as more of a “proof of luck” than a Proof of Work. For a miner to solve the Cuckoo Cycle Proof of Work, the machine must find a cycle of length 42. Once a cycle is found, an additional filter of the Hashcash algorithm is applied to the result from the found cycle. According to Tromp, Cuckoo Cycle miners calculate the speed of a machine by its measured graph rate, as opposed to the hashrate measurement used for calculating the mining speed of hardware for Blockchain’s such as Bitcoin and Ethereum. Hashrate is simply, how many hashes per second a miner is able to compute. The graph rate is, how many graphs that are able to be computed per second. Tromp further described fidelity, which is the probability that a miner will find a cycle of length 42, so Cuckoo Cycle miners measure the speed of their hardware using a combination of graph rate and fidelity to determine their mining speed.
Cuckoo Cycle Variants
The original whitepaper (9) for Cuckoo Cycle was written in 2014. Since then, there have been many new developments made with Cuckoo Cycle. Tromp originally thought Cuckoo Cycle was “ASIC resistant” Proof of Work. ASIC resistant simply means that an ASIC programmed for calculating Cuckoo Cycle would not necessarily give a miner a competitive advantage against other forms of mining, for example, compared against a GPU miner. However, Tromp created has now created two different variants: one variant of Cuckoo Cycle, called Cuckaroo Cycle, is ASIC resistant, another, known as Cuckatoo (10) Cycle, is ASIC friendly. There are at least two cryptocurrency mining machine manufacturers creating ASICs for Cuckoo Cycle Blockchains, in particular, for a blockchain known as Grin. Those two companies are Obelisk (11) and InnoSilicon (12).
What Coins Use Cuckoo Cycle?

There are a few projects that are implementing Tromp’s Cuckoo Cycle mining algorithm. MimbleWimble, the privacy preserving Blockchain protocol also makes use of Cuckoo Cycle. Aeternity (13), the unicorn Blockchain project based in Liechtenstein is using Cuckoo Cycle, and the hot privacy coins MWC and Grin (14) are implementing the Cuckoo Cycle.
There is even a research proposal named cuckoo-http (15) that is experimenting with Cuckoo Cycle to limit denial-of-service attacks against web servers. (16)
MimbleWimble
MimbleWimble is a privacy preserving blockchain protocol implementation and gets its name from the Harry Potter fictional book series. According to the official MimbleWimble documentation (17), “MimbleWimble as an idea was released anonymously. It’s a blockchain with Proof of Work but almost nothing else”. The first implementation of MimbleWimble was proposed by an anonymous online persona known as Ignotus Peverell, which is also the name of a fictional character from the Harry Potter series, thus following a similar anonymous origin to Bitcoin as being created by the anonymous Satoshi Nakamoto.
Grim
This first implementation of MimbleWimble eventually became known as Grin. Tromp was particularly excited about MimbleWimble and Grin and their decision to use Cuckoo Cycle as the mining algorithm. Tromp eventually became a core developer and contributor to Grin. Tromp described the coin emission model of Grin (18) to be of particular interest to him as he felt it had many advantages over other Blockchain’s coin emission models. However, we have a slightly different view. Grim has no hard cap on the coin supply, which makes it not scarce, and therefore, no different from other infinitely inflationary fiat currencies.
John Tromp, Making Computer Science Great Again
We asked Tromp how he felt to have such an influence of spawning an entire ecosystem within the mining industry. He humbly downplayed the significance he has actually had within the blockchain community but from where we’re viewing from, he has been very influential and is well respected Computer Scientist by many in the crypto space. When we asked Tromp about his perspective of the cryptocurrency mining industry, he described mining as a very tricky business and noted that many people have regretted getting into mining rather than just outright buying coins, and that novices should take note of this information before considering getting into the mining business. He also suggested that in order to succeed, one must understand the risks with running a mining operation as well as understand the need for having access to cheap long-term power contracts. With that said, we look forward to learning about future developments with Cuckoo Cycle, it’s variants, and the many up-and-coming blockchain projects such as Grin that are making use of Cuckoo Cycle.
(1) See https://tromp.github.io/
(2) See https://github.com/tromp/cuckoo
(3) See https://grin-tech.org/
(4) See https://github.com/mimblewimble/grin
(5) See https://github.com/mimblewimble/grin/blob/master/doc/pow/pow.md
(6) See https://en.wikipedia.org/wiki/Equihash
(7) See https://z.cash/
(8) See https://en.wikipedia.org/wiki/Hashcash
(9) See http://hashcash.org/papers/cuckoo.pdf
(10) See https://www.grin-forum.org/t/cuckoo-cycle-weakness-and-possible-fix-cuckatoo-cycle/738
(11) See https://obelisk.tech/products/grn1.html
(12) See https://www.innosilicon.com/html/a9-miner/index.html
(13) See https://aeternity.com/
(14) See https://www.beam.mw/
(15) See https://css.csail.mit.edu/6.858/2019/projects/kaza.pdf
(16) See https://github.com/AnimatedRNG/cuckoo-http
(17) See https://github.com/mimblewimble/docs
(18) See https://github.com/mimblewimble/docs/wiki/Monetary-Policy




