In cryptography, there is a theory that states that anything that can be done with a central party, can also be done without a central party. This refers to voting, auctions, banking, etc. For example, OpenBazaar is a decentralized version of eBay, Bisq is a decentralized version of Coinbase, and Bitcoin itself is a decentralized version of fiat currency. In a decentral network there is no ruler to make sure that everyone follows the rules. Instead, decentral networks rely on consensus mechanisms.
A consensus mechanism is the way that a group of people make a decision. For example, Bitcoin users need to constantly update their history of transactions in order to reflect new transactions and wallet balances. Consensus mechanisms enable strangers to come to an agreement by giving financial rewards or financial punishments. A major goal of consensus mechanisms is to stop users from double-spending the same coin. If a user could send the same Bitcoin to two different wallets, then the supply of Bitcoin could be inflated infinitely, which would result in a decrease in the purchasing power of the currency. In order to stop double-spends, every computer that maintains the Bitcoin blockchain needs to have the same information about which wallets hold what amounts of value.
Table 1: Consensus Mechanisms of the Top 100 Cryptocurrencies
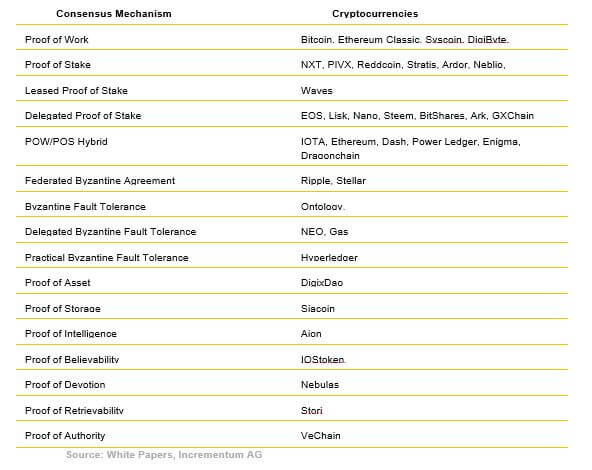
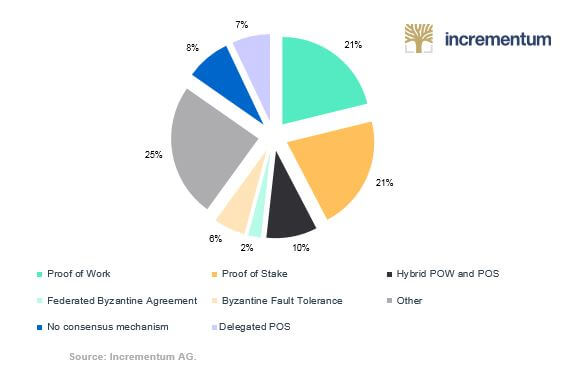
As shown in Table 1, around 17 different consensus mechanisms exist; however, none of them are perfect. So far, the most secure consensus mechanism is still the original one used by Bitcoin: proof of work. However, proof of work relies on miners, which can lead to centralization. Developers are constantly trying to beat proof of work because a coin that removes miners and their electricity consumption would splash big waves in the ICO market.
Figure 1: Consensus Mechanisms of the Top 100 Cryptocurrencies
Companies such as Visa and PayPal do not need to employ a consensus mechanism because they control the entire network. If someone uses their Visa credit card, the information is sent to a centralized database that is maintained by Visa. We trust these companies to protect our sensitive information and settle our transactions. Since Visa controls the network, they can reverse and censor transactions. In the 1970s, computer specialists began to explore other ways to solve this problem because they realized that even a central authority can be hacked by an adversary or corrupted from within. The two most popular methods for taking decentralized decisions in a cryptocurrency network are known as “proof of work” and “proof of stake”. However, dozens of consensus mechanisms exist including proof of authority, proof of space, proof of importance. All of these different methods are proposed solutions to the Byzantine Generals’ Problem.
Byzantine Generals’ Problem
Imagine there is a king in a castle defended by 300 soldiers. The castle is surrounded by five armies of 100 men each. Each army has its own camp in the surrounding hills and its own general. The generals need to communicate with each other in order to agree on an attack strategy. However, the generals cannot easily trust each other because they suspect that some of the generals are traitors. If they send a message on horseback from one camp to another with the time of the attack and strategy, then the disloyal generals could easily change this message and relay false information to the next camp. Sending a simple message is not secure because written text is easy to change. Misinformation could result in the traitors winning the battle because the different camps will attack at the wrong time or not attack at all.[1]
Nowadays, a conference call could replace the messenger on horseback, but the problem still persists. How can you be sure that the message is authentic and not tampered with? Authenticity refers to the problem that adversaries can fake phone calls or emails by pretending to be someone else. Tampering refers to the content of the message being changed, deleted, or read by an adversary.
To solve the Byzantine generals’ problem, consensus algorithms rely on two concepts. First, each of the generals would need to invest resources into the network, i.e. they need to have “skin in the game.” For example, imagine two businessmen decided to co-found a venture, and one refused to invest any time or capital into the venture. The invested partner would feel suspicious of his partner’s loyalty to the project. The same idea holds in a decentralized network. The second concept is that there must be a ledger of all previous communication that is “tamper-proof”. Tamper-proof refers to the ability of the computers to immediately detect when the history of communication has been changed or deleted. The digital version of the ledger is a blockchain that tracks each user’s transactions and links them using hash functions that ensure the data’s authenticity.[2]
To go back to the Byzantine Generals’ problem, one way they could ensure the loyalty of their comrades is to make each general invest a large sum of money in an escrow account that is impenetrable. Before a general sends a message, he must sign his name with a cryptographically secure signature that proves his identity. If any of the generals misbehave, the army will look at the message book and see the traitor’s signature. The traitor can still misbehave, but now he will suffer financially because the army will not give him back his deposit. This method of coming to a decentralized consensus is referred to as “proof of stake” because each general, or computer user in modern times, has a stake invested in the success of the network. Another option would be for the network to force each general to solve an extremely complex math problem before they can successfully sign and send a message. To solve the math problem quickly, the general would need to invest large sums of money in expensive mathematicians. This consensus method is called “proof of work” because the general proved that he invested scarce resources such as time and capital into solving the math problem.
Overview of Consensus Mechanisms
As shown in Figure 2, consensus mechanisms exist along two main axes, degree of centralization and degree of external anchor. The vertical axis ranges from centralized, where you need to trust a person or an organization to settle transactions correctly, to decentralized, where strangers settle transactions. For example, Bitcoin’s proof of work consensus mechanism is an example of a permissionless and public blockchain because an untrusted stranger can become a transaction validator and their identity does not need to be disclosed. Another example is Monero.
Figure 2: Centralization and Externality of Consensus Mechanisms
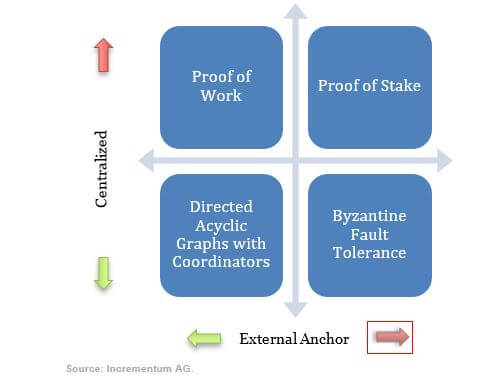
The horizontal axis refers to what kind of investment a user needs to pledge in order to gain power within the system. For example, Bitcoin requires users to pledge scarce resources in the real world in order to make decisions in the Bitcoin network. This is referred to as an external anchor. In contrast, consensus mechanisms that fall into the upper right quadrant, such as proof of stake, do not require external resources in order to make decisions within the network. This quadrant includes coins such as NXT and Peercoin. Ethereum is planning to switch from the upper left quadrant to the upper right quadrant over the next year.
On the other side of the spectrum in the bottom right quadrant are permissioned and private consensus mechanisms such as byzantine fault tolerance. IBM’s Hyperledger is an example of a data structure that allows the creator to specify who will settle transactions. A company that uses Hyperledger or Microsoft’s Blockchain as a service will know the identities of the people that they select to control the network, and the users of the network will need to trust these people. These systems are centralized, and they do not have external anchors. In the bottom left quadrant are coins like IOTA, Byteball, and Hashgraph. These coins have witnesses and coordinators that centralize the system; however, they still require the validators to pledge external resources in order to gain power within the network. The most common consensus mechanism is the directed acyclic graph structure combined with proof of work to prevent Sybil attacks.[3]
Proof of Work (PoW)
In the case of Bitcoin, you can think of the Byzantine Generals as different Bitcoin wallets. Computers that run the Bitcoin software use the proof of work consensus algorithm to come to an agreement on which payments are valid.
According to Hristian Hristov at the BlackSeaChain Conference, proof of work is
“a piece of data which is difficult (costly, time-consuming) to produce but easy for others to verify and which satisfies certain requirements. Producing a proof of work can be a random process with a low probability so that a lot of trial and error is required on average before a valid proof of work is generated.”
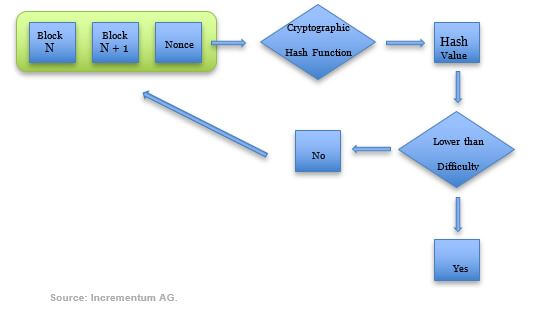
If Mark wants to send 5 Bitcoins to Demelza, the entire network must ensure that Mark has the 5 Bitcoins and that the transaction is being signed with Mark’s digital signature. Bitcoin nodes come to an agreement every ten minutes about which transactions are valid in a process known as “mining”. Before confirming a new block of transactions, the miners compute hashes until they find a desirable number that is less than a specific number set by the software protocol called the difficulty target. In the Bitcoin protocol for example, miners must find the right “nonce”, or arbitrary number, that produces a hash lower than the difficulty target set by the software. This is called a hash-puzzle because the miner must add the nonce to the hash of the previous block in the blockchain. The computational output is a number which basically falls into a target space which is comparatively small in relation to the large output space of the entire hash function.[4] This number becomes that block’s identification number, which is used as an input in the next block’s hash puzzle.
Figure 3: Proof of Work Computation
Proof of work uses two main types of financial rewards to incentivize users to maintain the network: rewards and transaction fees. The first miner to find a hash that is lower than the given difficulty target will be entitled to “print” new Bitcoins and receive the transaction fees that the senders paid to the network when they broadcasted their payments. The first transaction of every block is a “coin-creation transaction”. The coin-creation transaction allows the miner of the block to mint new Bitcoin and to send these new Bitcoin to his or her wallet. In 2016, the value of the block reward was about 25 Bitcoins.[5] However, this rate drops roughly every four years and is currently 12.5 Bitcoins. The block reward incentivizes honest behavior because the coin-creation transaction will only be valuable if it is accepted by the other users maintaining the network. The second reward is the transaction fee. When users send Bitcoin transaction they attach a fee. The higher the fee, the more likely a miner will include the transaction in their candidate block, which means the confirmation time of the transaction will be faster.
Figure 4: Bitcoin Minig and Transaction Revenues
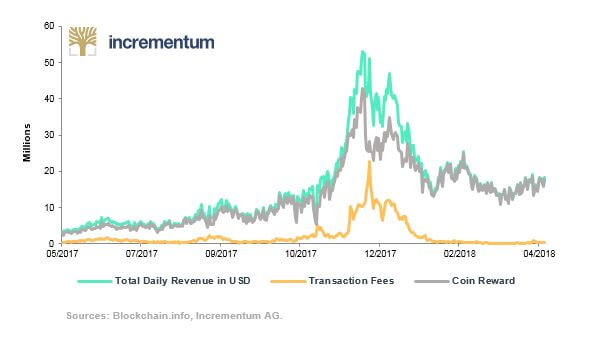
However, Bitcoin’s proof-of-work algorithm has disadvantages. First, there are several attack vectors that adversaries can exploit including:

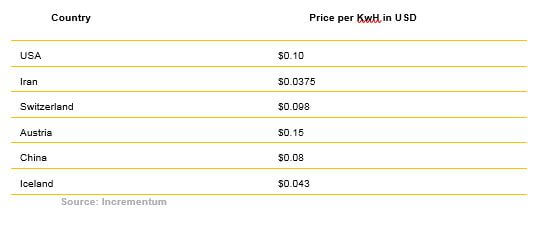
Second, the network uses large quantities of energy and hardware equipment, which have been estimated to cost approximately $400 million per year. Since more and more entrepreneurs are joining the mining industry, the difficulty of finding a Bitcoin block continuously increases. Consequently, the electricity a miner must buy to find a block is constantly increasing. This is why mining has naturally become centralized in countries where electricity is cheap. Table 2 shows the cost of electricity in several counties.
Like gold, Bitcoin uses electricity and capital equipment to mine new coins. The probability of randomly being chosen to create a block and receive a reward is equal to each miner’s amount of mining power divided by the total amount of mining power on the network. The more power the mining hardware consumes, the higher the hash rate. This results in a higher profit from mining. The parameters used to calculate include: difficulty factor, hash rate (TH/s), BTC/USD Exchange rate, pool fees in %, hardware cost (USD), power (watts), power cost (USD/kWh).[1]
[1] See “Is Bitcoin Mining Profitable in 2018,” Ofir Beigel, 99Bitcoins, 2018.
Table 2: Cost of Electricity by Country in 2018
Proof of Stake (PoS)
Unlike Bitcoin or gold, proof of stake allows the users with the largest holdings to create coins out of thin air. In a proof-of-stake system, the probability of receiving a reward is equal to the fraction of coins held by the user divided by the total number of coins in circulation. Several varieties of proof of stake exist including leased proof of stake and delegated proof of stake.
Both systems achieve similar outcomes; however, proof of work incurs a negative externality on the environment. Then why are people still using proof of work? The highest market capitalization coins all rely on proof of work but proof of stake is gaining popularity: Ethereum, the second largest market capitalization coin, is expected to switch from proof of work to delegated proof of stake during the next year.

In addition to attack vectors, proof of stake has not been well tested on the market. Although many supporters of proof of stake claim that it is less centralized than proof of work, this is not necessarily true. Since investors receive interest on their long positions, proof of stake encourages hoarding more than proof of work. As Andreas Antonopoulos explained during the Wisma BeeOn Group in Kuala Lumpur, Malaysia, proof of stake allows the rich to get richer. This has a centralizing impact on the holders of the cryptocurrency. In contrast, proof of work miners are forced to release a certain number of coins to the market in order to invest in new mining hardware and to pay electricity bills. This allows a relatively constant amount of newly minted Bitcoins to hit the market every day.
Conclusion
The main trade-off that cryptocurrencies face is between centralization and efficiency. The more centralized the decision-making process is, the faster the decision can be taken and the more scalable the network is. On the other hand, the less centralized a network is, the longer it takes to come to a consensus. This is not unlike the dichotomy between dictatorships and direct democracies. When the hierarchy between shareholders is flat, unanimous decision making is difficult to achieve. Although the introduction of counterparties may not be a problem in every case, the original goal of the blockchain technology was to create consensus without intermediaries. Miners, oracles, witnesses, delegates, or stakers all centralize the system to some degree.
A consensus mechanism that could remove proof of work’s electricity use without introducing a directed acyclic graph coordinator would make huge headlines in the cryptospace. MIT cryptographer, Silvio Micali, reports that his consensus mechanism, Algorand, achieves decentralization and security simultaneously. We plan to keep this algorithm and coins that employ it on our radar. Also, coins such as Tezos and Dfinity promise to embed governance at the protocol level, which may enable decentralized shareholders to come to a consensus faster. While we are optimistic about the ability of developers to overcome the scaling problem in the long run, we recognize that proof of work’s proven track record of at least ten years makes it the undefeated champion of consensus mechanisms. However, governments may crack down on the use of electricity to mine cryptocurrencies, therefore, we recommend holding a range of cryptoassets with different consensus mechanisms.
[1] See “Bitcoin and the Byzantine Generals Problem“, Patricia Estevao, We Use Coins, July 13, 2015.
[2] IOTA and Byteball use a directed acyclic graph instead of a blockchain to record transactions.
[3] Witnesses & coordinators are meant as a temporary measure until the network reaches scale according to developers; however, the path to decentralization is not clearly defined.
[4] Narayanan, A., Bonneau, J., Felten, E., Miller, A., & Goldfeder, S. (2016). Bitcoin and Cryptocurrency Technologies. New Jersey: Princeton University Press.
[5] Ibid.




