“There are a lot of investors where custodianship was the final barrier. Over the next year, the market will come to recognize that custodianship is a solved problem. This will unlock a big wave of capital.”
Kyle Samani
Hedge Fund Manager at Multicoin Capital

In the January 2019 edition of the Crypto Research Report, we extensively covered institutional grade cryptocurrency custody. We interviewed three firms in the space including Crypto Vault AG, Crypto Storage AG, and Coinfinity. This article explains custody from the perspective of a user, including information on how to store keys privately, and what questions to ask when considering using a storage company.
Storing Digital Assets in a Digital High Security Vault
| “Custodians are necessary as the next step towards crypto-assets being seen as a safe and attractive financial asset option for large FIs and perhaps for market confidence in general… Major institutional custodians providing a secure place to store large amounts of crypto-assets could provide the protection necessary to reduce the risk of hacks and increase the trust of the investing public in crypto-assets.” Attorneys at Perkins Coie |
Storing your gold or other physical assets comes with two options: either at a facility you completely control in all aspects (self-custody) or at a service provider, who holds the assets in your name secured in a facility you have no access to (service custody). The same principle applies for storing your digital assets like bitcoin. However, digital assets require a digital vault to provide the highest security standards. But what exactly needs to be stored safely in case of digital assets? It is the so called “private key” which provides access and control over the digital asset and thus the right to transfer it to someone else. In the case of Bitcoin, the private key is a 256-bit number represented in hexadecimal form. Storing these keys is basically a physical issue as they could be simply written on a piece of paper or engraved in metal and put into a safe deposit box to limit physical access and digital exposure to the internet where they could potentially be accessed and copied by a hacker. As a private key is needed to sign a transaction (prove ownership), software is required to execute the signature generating process and the key needs to be revealed to this software. In order to facilitate this procedure, specific hardware wallets were introduced which enable not only a hardware secured environment for generating the necessary signatures without exposing the key to the internet, but also can handle an infinite amount of keys deriving from a master private key following a standardized process. This standardization of key derivation enables users to backup just the master private key and recover all necessary keys on a new device in case of malfunction or loss.
| Using only N of M private keys makes it possible to store e.g. another key somewhere as a backup. Should one of the keys be stolen or lost, the secured Mth key can be retrieved. |
The next step to attain an even higher level of security would require one to build something which could be described as a digital vault. A digital vault typically involves the creation of multiple master private keys and storage of them on special hardware wallets with secure elements at different geographic locations.
The transaction then needs to be signed by N out of M private keys depending on the spending rules implemented when originally receiving the funds. This concept is called multisig – short for “multi signature scheme”.
In order to deal with malfunction of key storage hardware, a proper backup plan is crucial. The most common practice is to either perform a so-called key rotation or to securely store encrypted backups to be able to recover the master private keys. Both methods come with advantages and drawbacks.
Figure : Example of a “Multisig-Scheme”
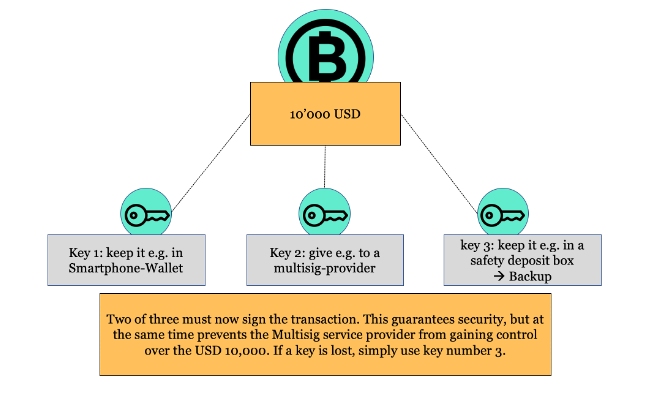
Source: Incrementum AG, Daniel Wingen
The execution of a key rotation becomes necessary if one decides that the master private key should never leave the secure element of the hardware wallet, which makes backups impossible. This is great for reducing attack vectors as long no device malfunctions, but if there is an incident, all funds need to be moved to a setup of completely new generated master private keys. Moving millions or even billions worth in digital assets is a very critical and expensive endeavor which takes time and introduces a lot of attack vectors if not planned and executed accurately. Backing up the master private keys on the other side also opens a new attack vector for collusion or social engineering to extract the private keys.
Figure: Two Major Ways of Protecting Against Hardware Malfunctions
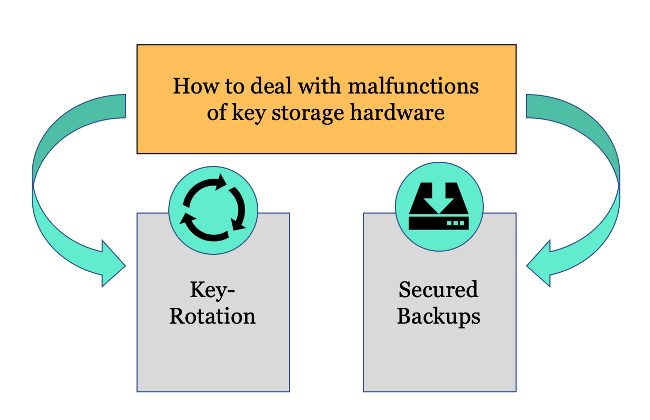
Source: Incrementum AG, Daniel Wingen
| A key rotation scheme means that you have to replace the entire set of keys. This is because if you lose one of three and you need two out of three keys to sign a transaction, you have to act quickly. The coins need to be moved to a new address where you again own all three keys, because if one additional key would be lost, all the coins are lost forever. |
| Social engineering can be described as a psychological strategy in which attempts are made to gain access to digital safes through targeted manipulation. Attempts in this context means that company employees come together internally to gain access to digital safes. |
This means a well-functioning digital vault for digital assets requires an elaborate technical solution for:
- key generation
- signing procedure
- the storage of private keys (and backups) at different geographic locations.
Social engineering can be imagined as a psychological strategy in which attempts are made to gain access to digital safes through targeted manipulation. But apart from that, a well-designed digital vault should have further features to make it more secure. First, we have a closer look on how the private key is stored ideally before we go into more details on the signing of transactions.
| “From the perspective of IT security, the aspects of recognition performance and security are of particular importance when considering biometrics.” Federal Office for Information Security, Germany |
In general, it is very common to secure devices which hold the private keys in a physically secured bank vault which is similar to gold storage, however, there are some important differences. To begin, the devices on which the private keys are stored should be protected with additional digital security measures. Only specific predetermined persons may access the device with identification through biometric data such as fingerprint. In addition, entry is only allowed at specific predefined times or else if specifically authorized by the board of directors of the company operating the digital vault. This reduces the probability of unwanted signature generating events virtually to zero.
| Cold vs. Hot Storage Custody of Cryptocurrencies: If the wallet is connected to the Internet, this private key is exposed to potential hacker attacks. Because of the online connection to internet, this type of storage is called hot storage. A cold wallet, in contrast, is a storage space that is not connected to the Internet. The keys with which you can manage your digital money are stored offline. This of course reduces the risk of DDoS attacks and hacker attacks considerably. |
Most importantly, only transactions authorized by a predefined quorum of decision makers may be signed with the corresponding private keys. In order to achieve that, typically an additional cryptographically secured authorization layer is put in place. This layer is an addition to the cryptography securing the digital asset itself. Each digital vault operator defines its own authorization processes which can be adapted to different internal processes or client needs. For example, one could agree that the authorization process of a transaction must involve at least three people on the client side signing a transaction approval with their individual authorization keys stored on personal security devices. The authorization process should involve biometric data or other second factors like chip and pin. In order to prevent theft by colluding employees within a custodian, it is reasonable to include a business logic that technically requires the authorization by the client. However, the board of directors could mutually change the business logic of the authorization layer to access the digital assets without authorization by the client. They could even just access the master key backups directly if not properly secured through profound business continuity management (BCM). This is why it is important to rely on a custody provider with trustworthy management that is audited by regulatory authorities. Also, the custody provider must show a thoughtfully implemented segregation of duties since human interaction is the most critical point of failure.
| An example of such a BCM rule could be this: Nobody can access the safe deposit box which stores the backups without having registered with the safe company a week in advance. Upon this “one-week in advance registration”, everyone in the company would receive an email/SMS message announcing the registration. Then, only one person with biometric data and/or two-factor authentication can access it on that day at that specific time. In addition, in order to change this rule with the vault company, a quorum of management approvals through formal request and verification would be required. A similar approach could be established for hardware wallets to access them for firmware updates. This could be in the form of a certain quorum of signatures from managers that would be required to overwrite the bootloader and allow firmware updates etc. |
If you plan to store your digital assets at a custody service provider, it is of utmost importance to check their technical solution on whether it is designed according to industry standards which reduces risk for loss, theft and fraud of private keys to the lowest possible. A good custody provider should provide the following:
- A digital vault (cold storage) with at least 2 out of 3 multisig.
- Distribution of partial keys on different geographic locations in countries which are considered to have a stable system in regard to respecting proprietary rights (USA, Singapore, Switzerland, Germany, etc).
- Safe backup of the private key which should again be distributed geographically, or alternatively, a sophisticated key rotation scheme.
- Trustworthy management audited by regulatory authorities.
- Authorization layer that requires customers’ consent to sign transactions.
Figure: Services of a Good Custody Provider
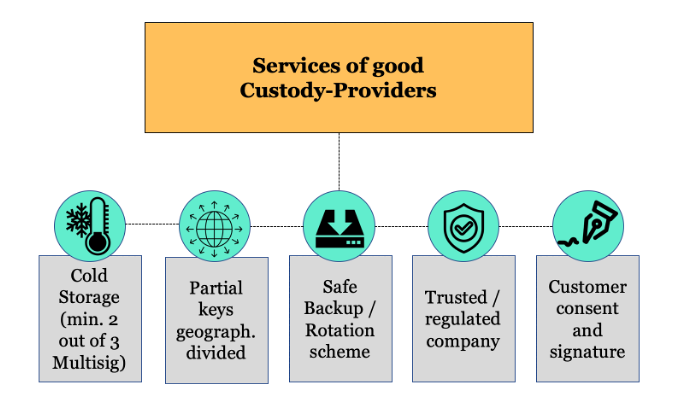
Source: Incrementum AG, Daniel Wingen
Self Custody vs Serviced Custody
| “James Howells is a multi-millionaire – and somehow not. Thousands of Bitcoins are slumbering on his hard drive, which is now worth 75 million euros. The catch: The hard disk is buried in a dump.” N-TV.de |
| The obligation to hold the assets under management means no more than that the funds must be placed externally within a depositary. |
The above chapter showed that the process of setting up and maintaining a digital vault to secure a significant amount of digital assets does require a lot of specialized knowledge and well thought through security procedures. Such a complex setup is currently hardly feasible for a private person or small company without investing a significant amount of resources in research and development. This will very likely change in the future, but currently self-custody always comes with reduced security if proper knowledge and secure technical implementation is absent. To achieve a certain level of security, one has to know the technology quite well and understand the digital assets specific mechanics of the public private key methods used. Then, one needs to store the private key safely in a way that it cannot easily be stolen or lost. If the private key is lost, then the digital assets cannot be accessed by anyone anymore which equals a total loss of the assets. Understanding the technical mechanisms of accessing digital assets with a private key requires time and can be very difficult to grasp for the less tech savvy people. In addition, one needs to make sure that one’s heirs may obtain access but only when the time has come. This problem can be easily solved with serviced custody, but it is rather difficult to solve in self custody. Self-custody for corporations is even more complex since access to the private keys must be split and distributed to several people to ensure that no single person has access to all funds. If only one person had access and this person gets involved in a deadly accident, then all funds of the corporation would be gone – a situation which shall never occur. Depending on the jurisdiction, financial service providers are even obliged by regulation to store their assets under management in custody. In Germany, however, the separation between financial service companies and custody was eliminated by law.
The idea behind Bitcoin, however, is decentralization and censorship resistance. Bitcoin technology hands people back their financial self-sovereignty and creates a level playing field where every individual, company or bank has the same entry barriers to transfer the asset globally with near instant settlement – but only if one controls the private keys. In line with this, there is a common perception of “not your keys not your bitcoin” which encourages self-custody.[1] We see it as reasonable to have a balanced perspective on self-custody and serviced custody by looking at the pros and cons of both. Deciding on the custody solution for your digital assets should include:
- your knowledge on the technical solution,
- the general pros and cons of the options as well as
- the amount of funds to be stored
- and the specific use case.
Private individuals can simply store smaller amounts of digital assets with consumer grade hardware wallets which are easy to use and provide reasonable security if handled with care and a basic knowledge of the mechanics involved.
Regulatory Developments in DACH (Germany, Austria, Switzerland)
| “New obligated parties (of the 5th AML Directive) are platforms for exchanging virtual currencies and providers of electronic purses (wallets) for virtual currencies (e.g. Bitcoin) etc.” Paytechlaw.com |
The 5th Anti-Money Laundering (AML) Directive is the most important regulation for digital assets in the European Union so far. The directive lays out the anti-money laundering obligations imposed on cryptocurrency businesses which includes the requirement for Know Your Customer (KYC) processes to identify customers. This legislation provides more clarity for national states and businesses on how digital assets are regulated.
Germany pioneered the issuance of crypto custody licenses that came into effect on the 1.1.2020. Crypto custodians now have to apply for a “Kryptoverwahrer” license to provide custody services for digital assets, however, existing custodians are allowed to keep up their business until a decision on the license application is made by the BaFin, the German financial market authority.
Austria made amendments to their Austrian Financial Markets Anti-Money Laundering Act (“FM-AMLA”) and the Beneficial Owners Register Act (“BORA”). Crypto Custodians need to be registered with the Financial Market Authority since 10.1.2020. In Austria, no license is needed to provide crypto custody service. The AML amendments merely require enhanced due diligence measures if a high-risk third country is involved in a transaction.[2]
The 5th AML directive does not apply to Switzerland since the directive is EU law. According to the Swiss Financial Market Supervisory Authority FINMA, “Switzerland has always applied the Anti-Money Laundering Act to blockchain service providers”.[3] In 2019, FINMA granted SEBA Crypto AG and Sygnum Bank AG a full banking and securities dealer license.[4]
Global State of Custody Service Providers
| “[Custody] is the missing piece for infrastructure – it’s a treacherous environment today. Hedge funds need it, family offices need it, they can’t participate in digital currency until they have a place to store it that’s regulated.” Mike Belshe, Co-Gründer & CEO von BitGo |
We have identified more than 20 custody providers operating at the end of 2019 with Coinbase, BitGo and Bakkt being the largest. Coinbase has become famous with its exchange services. The company is managing assets with a value of USD 7bn in 2019.[5] Bakkt is created by CE the company behind NYSE and known for introducing Bitcoin futures that are fully backed with “physical Bitcoins”- in line with the company’s name. This means that the bitcoin to fulfill a buy position that is scheduled for the future is already available by Bakkt. BitGo provides clearing and settlement services that are connected to several exchanges, OTCs, hedge funds and more. The customer may decide which party to choose and to settle a trade with while the funds are locked during settlement which minimizes counterparty risk.
Figure: Projected Tokenized Market Volume until 2027
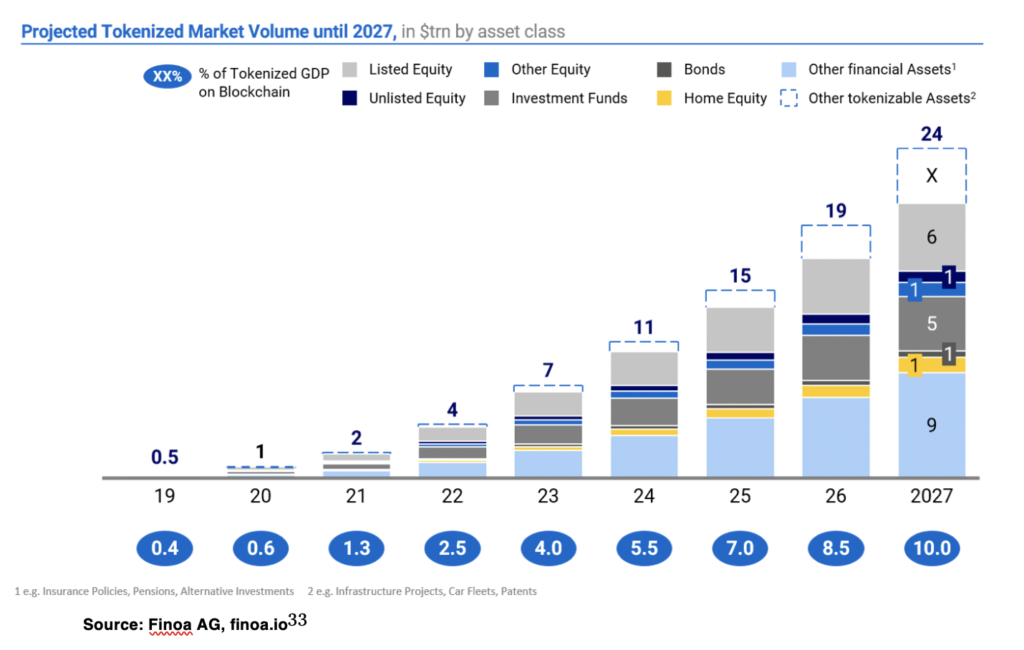
Source: Finoa AG, finoa.io[6]
In Germany, ING Diba, the most famous direct bank, announced to apply for the crypto custody license[7] as well as Solaris Bank, the banking as a service provider for startups[8]. According to Finoa, a Germany based custody provider, the amount of tokenized assets under custody will reach 1 trillion by 2020 and 24 trillion by 2027. However, these statistics mostly focuses on equity, debt and tokenized real estate, neglecting the expected increase of Bitcoin market capitalization according to the Stock-to-Flow model.[9]
[1] A detailed report on self-custody can be found here for free: https://www.smartcustody.com
[2] https://www.schoenherr.eu/publications/publication-detail/the-impact-of-the-5th-anti-money-laundering-directive/
[3] FINMA Guidance 02/2019https://www.finma.ch › finma-aufsichtsmitteilungen
[4] https://www.caplaw.ch/2019/finma-grants-banking-licenses-to-new-swiss-crypto-banks-introduces-new-strict-aml-rules-regarding-payments-on-blockchain/
[5] https://blog.coinbase.com/coinbase-custody-acquires-xapos-institutional-business-becoming-the-world-s-largest-crypto-2c1b46fc94c4
[6] https://hackernoon.com/market-outlook-on-tokenized-assets-a-usd24trn-opportunity-9bac0c4dfefb
[7] https://www.reuters.com/article/us-crypto-currencies-ing-exclusive/exclusive-ing-working-on-digital-assets-custody-technology-sources-idUSKBN1YF2GN
[8] https://solarisbank.pr.co/184220-solarisbank-launches-subsidiary-solaris-digital-assets-to-drive-adoption-of-crypto-and-further-digital-assets
[9] https://medium.com/@100trillionUSD/modeling-bitcoins-value-with-scarcity-91fa0fc03e25




